
Recently, a team of researchers at Google announced that they had successfully created a SHA1-collision. Our VPN experts are going to outline what that means and what security implications it has for VPN users.
What SHA1 is used for
SHA1 is a cryptographic hash function that is used to verify signatures and other security-related files. Basically, it lets you quickly check that the file or digital signature you’re being shown is actually the real deal.
What’s all the fuss about?
In the last few years, researchers theorized that it might be able to create a fake file that matches a genuine file’s SHA1 signature. It was all just a matter of computing power and given the way technology works, that it would be possible in the next few years.
At that’s exactly what has happened: the Google team used a clever technique and Google’s vast server infrastructure to create a fake PDF file with the same SHA1 hash as their reference file.
What does SHA1 have to do with VPN?
When using a VPN, the server and VPN app go through several steps that let each side verify they’re talking to the right person. There’s Phase 1, during which both sides set up a secure channel to talk over. Then they use that during Phase 2 to establish the actual VPN tunnel used to transmit encrypted data.
SHA1 can be used in both of these setup phases to verify the authenticity of the data being exchanged and is configured by default for many VPN vendors.
So is a VPN that uses SHA1 at risk?
For single files like their PDF example or website certificates, Google’s research definitely shows that switching to SHA-2 is an important and necessary step.
However for VPNs, the attack is not feasible due to the short key lifetimes used:
In Google’s research, they needed the equivalent of 6500 single CPU-years to create their fake file.
In your VPN tunnel, a SHA1 hash is only used for 1 hour on average, before it is swapped for a new key. And the hash algorithm is used to verify a packet that has already been encrypted. So an attacker could only use this attack to sneak a fake packet into your data - and they'd have to compute in within 1 hour. To actually read your data would still be impossible, as the encryption algorithm means there are effectively two layers of security an attacker would need to break.
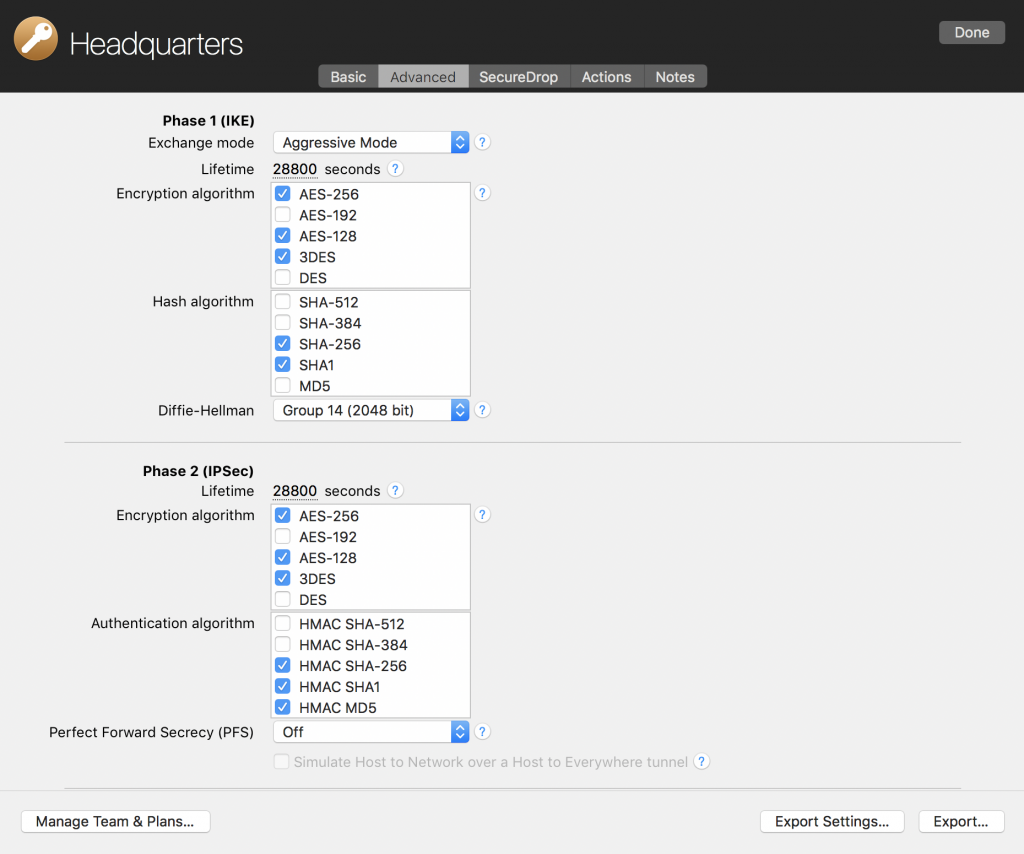 Security setup within VPN Tracker 365
Security setup within VPN Tracker 365
Extra protection: use SHA-2 with your VPN
The latest VPN gateways also support SHA-2 hashes (e.g. SHA-256, SHA-384 or SHA-512). These are more modern, highly secure SHA variants that can’t be broken. SHA-2 has been supported in VPN Tracker since 2015 and is in our default configuration for many popular VPN vendors, including SonicWALL.

Secure: SonicWall TZ600 Gateway (uses AES-128, AES-192 and AES-256 with SHA-256)
The future
We always recommend using the strongest encryption available to you. So switching to SHA-2 algorithms if your VPN gateway supports it is a good idea. However SHA1 is still secure, provided you use a relatively short key lifetime and, more importantly, always pair it with a strong encryption algorithm (such as AES-128, AES-192 or AES-256).




